Information is the core of businesses. Internet use has become widely common. Smaller organizations are also looking for cloud computing solutions and access to sophisticated data to solve business challenges. With the help of information, it is possible to gain a competitive advantage. Raw data has real value. The system uses this data to curate and process information.
With data security management system, it becomes more apparent information has become less secure there is a great amount of information to be managed and with this hackers and criminals find it easy to look for targets. So we can’t afford to take information security lightly.
As the tech grows there has been a massive spike in cyber attacks and that’s the reason all the companies want to increase their security. In this blog, we will talk about how to prevent cyber threats through security management systems.
What is ISMS?
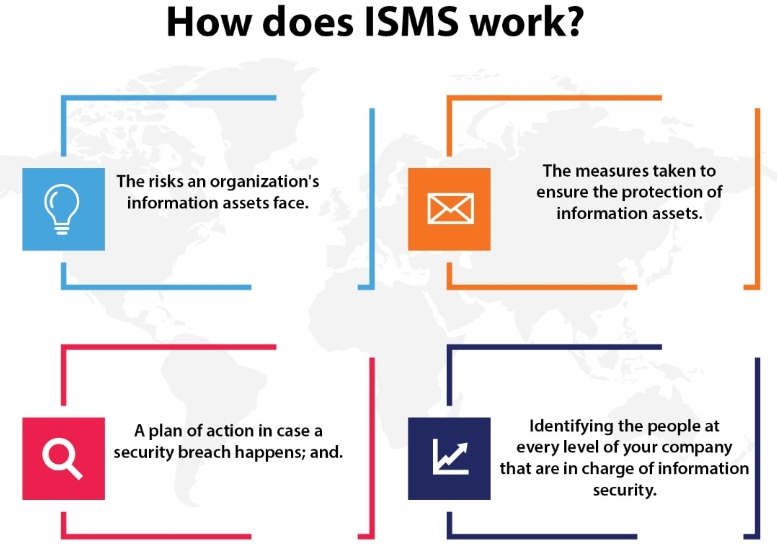
An information security management system or ISMS explains and illustrates an organization’s information security and privacy approach. It assists you in identifying and addressing the dangers and opportunities surrounding your important information and any other linked assets. That, in turn, protects your organization from security breaches and minimizes the impact of any disruptions that might occur.
With the help of information security management software, you can comply with various regulations, including the General Data Protection Regulation (GDPR) and ISO 27001. The CIA model is a common model used to design an ISMS. The ‘C’ in CIA stands for confidentiality. No unauthorized people can access or use the data in any way that is not explicitly permitted. The ‘I’ stands for integrity. This means that the data has to be free and stored in a secure location. The ‘A’ stands for availability. That means it must be straightforward for authorized individuals to access and use the data.
Why is an ISMS Essential For Your Organizations?
An ISMS shapes your organization’s data privacy and data management structure. This allows your organization to identify risks such as data breaches, and what would happen in case of accidental loss of data. Having an ISO 27001-compliant ISMS means building trust with potential customers in pitches and RFPs. Stay GDPR compliant, ensure legal and regulatory compliance, increase your resilience to cyber attacks and errors, and adapt to new security threats.
ISO 27001 is also important because it helps organizations manage and protect their sensitive information reducing their risk of data breaches, cyber-attacks, and other security incidents. It assists organizations to comply with legal and regulatory requirements related to information security.

How Do Data Security Management Systems Protect From Cyber Threats?
In the face of increasingly complex cyber threats, it’s essential that the security measures you implement are part of a wider strategy, aimed at helping your organization prepare for, and respond appropriately to, whatever might happen. This is why a defense-in-depth approach to data security is so important. Companies must prevent unauthorized access to their data and guard against efforts to manipulate or corrupt data, throughout the data life cycle from creation to destruction. Insider threats are one of the biggest threats to data security. An insider threat might come from a current or former employee or a third-party partner or contractor.
Organizations need to take a defense-in-depth approach to their data security strategy, which means using a combination of tools, techniques, and policies. There are various data security tools organizations can consider to keep their data secure. One is data lifecycle management (DLM). A DLM tool uses automation to apply established policies to data. DLM products ensure digital information stays accurate, confidential, secure, and available from the moment it’s created into the time it’s no longer needed and is destroyed.
Patch management software is another helpful data security aid because it keeps data safe by detecting and fixing vulnerabilities. The type of vulnerabilities data packers love to exploit so they can steal or corrupt an organization’s data. Analytics tools focus on user behavior. These types of tools often called user behaviour analytics are user and entity behaviour analytics that work by flagging attempts to gain authorized access.
These tools can also alert security systems when sensitive data is accessed an unusually high number of times which can help organizations detect things like lateral network attacks, compromised user accounts, and insider threats. But one of the most effective data security tools is education such as security awareness and training programs. After all intentional and unintentional mistakes by staff contractors and partners pose one of the greatest threats to data security.
Data or information security management systems are process-oriented, and they are always the responsibility of management. It’s always a top-down approach, though the actual implementation can be delegated. Depending on your business goals management selects the procedures and methods to ensure information security and corporate activities. Your management team must regularly examine the scope and progress of the measures implemented.
The goal of an ISMS is not to achieve maximum information security. Rather it’s to achieve the organization’s desired level of information security and risk appetite is key here. Your business needs to understand its data, the risks, and the financial impact of an incident. Based on this knowledge, the management team must decide to what extent these risks should be reduced by ISMS.

What is ISO 27001?
ISO 27001 is one of the most popular security standards in the world. As it protects your business from threats, make sure your employees feel safe and help you close more sales deals. ISO 27001 is an international security standard designed to protect businesses from data security threats. It is the management system which sets out how you manage your information security. It includes things like policies risk management, continuous improvement leadership buy-in, how you structure, how you report, how you monitor and how you measure, so it is the heart of any organization.
ISO 27001 provides a practical framework for protecting your information assets. It demonstrates to interested parties such as customers, regulators and investors that you can appropriately secure information in your position. ISO 27001 provides reassurance to internal and external stakeholders that information security is being managed effectively. Thus, it helps to ensure good corporate and security governance.
Conclusion
Where cyber threats are increasing rapidly, it is essential that the security measures you implement are part of a wider strategy aimed at helping your organization prepare for and respond appropriately to whatever might happen. This is why a defense-in-depth approach to cyber security is so important. If one of your defensive layers is breached there’s another to contain the damage. ISO 270001 provides a framework to help organizations of any size or industry. It protects business information systematically and cost-effectively by the adoption of what’s known as an ISMS. With the right guidance and plan in place, you can achieve ISO 27001 compliance and protect your business from data security threats.






