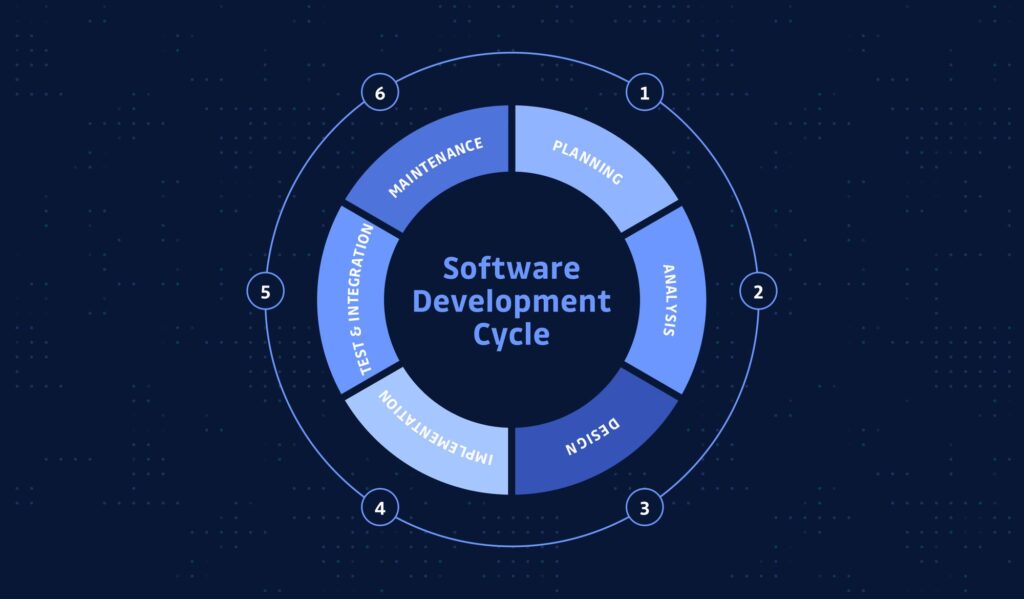
Software vulnerabilities discovered late in the development process can be costly and disruptive. Emergency patches, delayed releases, and potential data breaches are common consequences. Implementing a Secure Software Development Lifecycle (Secure SDLC) embeds security measures directly into every stage of development, preventing risks from reaching production and supporting consistent, reliable software delivery.
Embedding Security from Design to Deployment
A practical Secure SDLC begins at the design phase. Threat modeling identifies potential attack vectors, influencing architecture decisions and guiding teams toward more resilient system designs. Abuse case analysis examines how a system could be misused, uncovering risks that standard functional use cases might overlook.
During development, secure coding practices and automated checks integrated into CI/CD pipelines ensure vulnerabilities are detected early. Each build undergoes consistent security controls, allowing teams to identify and resolve issues in real time. By the testing phase, focus shifts from reactive problem-solving to verification, significantly reducing last-minute patches and costly fixes.
Continuous monitoring and feedback loops between development, QA, and security teams help maintain alignment. This collaborative approach reduces miscommunication, avoids duplicated efforts, and accelerates release cycles while maintaining high-quality, secure software.
Collaborative Security Practices
Secure SDLC relies on ongoing collaboration between development, QA, and security teams. Security is embedded into daily workflows rather than treated as a separate stage. Key practices include:
- Risk Analysis & Mitigation – Proactively identifying potential system disruptions and implementing preventive measures before they escalate.
- Threat Analysis & Modeling – Simulating real-world attack scenarios to reduce vulnerabilities early in the lifecycle.
- Abuse Case Analysis – Spotting unconventional misuse scenarios that could lead to breaches.
- Secure CI/CD – Automating security controls across pipelines to catch issues continuously and maintain software integrity.
- Code Review and Documentation – Maintaining clear documentation of security decisions and review processes ensures that knowledge is retained across teams and reduces the likelihood of repeated mistakes.
Infrastructure Review as a Complement
While Secure SDLC focuses on securing the software development process, the surrounding infrastructure also plays a critical role in overall resilience. Conducting an Infrastructure Review ensures that servers, networks, and configurations support secure software operation. By assessing and hardening the underlying environment, organizations reduce the likelihood of external factors undermining application security. Combining software-level security with infrastructure evaluation creates a holistic protection strategy that addresses both code and environment.
Benefits of Secure SDLC
Adopting Secure SDLC offers measurable advantages:
- Fewer late-stage vulnerabilities and emergency patches, reducing downtime.
- Enhanced collaboration and efficiency across development, QA, and security teams.
- Faster delivery of applications with embedded security, avoiding delays caused by unplanned fixes.
- Improved overall system reliability, maintaining user trust and protecting sensitive data.
- Alignment with compliance and regulatory requirements, supporting audits and certifications.
By integrating security practices throughout the software lifecycle and complementing them with infrastructure assessments, teams can deliver software that is reliable, resilient, and ready for production. Secure SDLC transforms security from a reactive afterthought into a proactive foundation, enabling consistent, high-quality releases while effectively mitigating risks.